Tweet @24HourSupport for Twitter Help
 Did you know that 24HourSupport is on Twitter? We know that sometimes, you may not be in a talking mood and may want to hop on social media to see if you can get a quick answer to your broadband Internet and email questions.
Did you know that 24HourSupport is on Twitter? We know that sometimes, you may not be in a talking mood and may want to hop on social media to see if you can get a quick answer to your broadband Internet and email questions.
In steps @24HourSupport. Of course, you’ll need your own Twitter account to be able to get the help that you need, but that’s really easy. You can view this article on how to set up a Twitter account so that you can get started! Also, check out some of the tweets that we’ve sent out below:
Are you watching out for those pesky attachments in emails? Here's why you should. #viruses #malware #24HourSupport http://t.co/HHAfMpZarY
— Internet Help (@24HourSupport) March 10, 2014
What happened when you tried to set up your #Outlook2013? Get it set up right w/ these tips. #24HourSupport http://t.co/36HixleJvD
— Internet Help (@24HourSupport) March 7, 2014
#Linksys Routers Seeing Attacks from The Moon #Malware #TheMoon http://t.co/T7OSsQljjn
— Internet Help (@24HourSupport) March 4, 2014
Tinkering with your #smartphone this morning? Tweet us pics of you browsing the #24HourSupport site!
— Internet Help (@24HourSupport) February 25, 2014
Trying to get your #AppleTV connected to #WiFi? We want to help. Try these steps. #24HourSupport http://t.co/pdCwxNhSRw
— Internet Help (@24HourSupport) February 17, 2014
Google Drive Users Latest Target in Google Docs Phishing Scam
 By now, most of you are aware of phishing scams and how to protect yourself from them, but the scam list just got longer for Google Docs and Google Drive users. Symantec recently identified a phishing scam that can put Google users’ account information into the wrong hands if they aren’t cautious about the email links they click.
By now, most of you are aware of phishing scams and how to protect yourself from them, but the scam list just got longer for Google Docs and Google Drive users. Symantec recently identified a phishing scam that can put Google users’ account information into the wrong hands if they aren’t cautious about the email links they click.
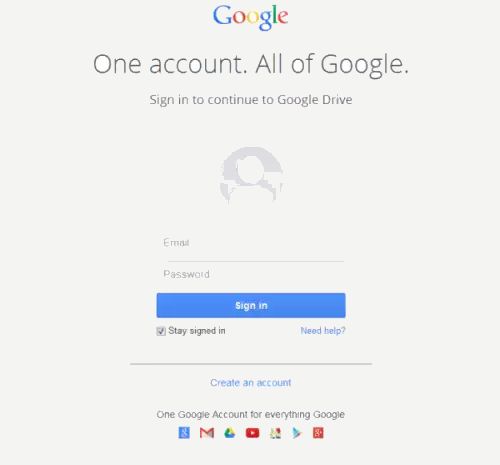
How Does the Scam Work
If your Google account is targeted, you’ll receive an email with the subject “Documents” that provides you a Google Docs link within the email. If the link is clicked, you’ll be redirected to a fake Google sign-in page like the one below that appears as a legitimate page and even has the google.com domain available in the browser’s address bar. This is the hook of the phishing scam that makes it seemingly believable. If, unfortunately, you fall for the scam and log into the fake Google sign-in page, a Google doc does appear but by then, your login information has been exposed and sent to a compromised server.
If you think you’ve already fallen for the scam, you can start off by changing your password to your Google account to a secure password of your choice. Of course, you should always make sure that your computer is protected with updated anti-virus and anti-malware software to keep security threats at a minimum. Set up a schedule so that scans are completed regularly. Also, always be cautious of any emails from senders you are not familiar with. Don’t open any files or click links unless you are confident the message is legitimate.
Have questions about this phishing scam or other Internet support help topics? Don’t forget to tweet your questions to @24HourSupport on Twitter.
Router Access Restrictions for Your Home Network
 Most often, everyone has a wireless home network because of the convenience that they provide. We take measures to secure the wireless network to keep unauthorized users from accessing the network, but what about those in your home whose activities you need to limit? What can you do to stop them from doing the things that make you cringe? Try router access restrictions.
Most often, everyone has a wireless home network because of the convenience that they provide. We take measures to secure the wireless network to keep unauthorized users from accessing the network, but what about those in your home whose activities you need to limit? What can you do to stop them from doing the things that make you cringe? Try router access restrictions.
In most wireless routers, there are features contained that allow you to set specific instructions on how you want the Internet and access to your wireless network to be used. If you don’t want the kids getting online after 9pm, set up a restriction that disables Internet access and makes them get out a book and read instead. If you want to keep certain computers or devices off your wireless home network, set up MAC filtering and only enter the MAC address for your most commonly used devices. There are likely to be various options that can be set up so that you can feel safe and protected.
Want to put your restriction skills to use? Try these helpful resources to find instructions on setting up access restrictions on popular router manufacturers.
Is Windows XP Really Coming to an End?
 Do you remember waaaay back in 2001 when Windows XP first came onto the computer scene? Everyone thought it was fantastic. The interface was a drastic change from the previous versions, it was packed with features, and the security of the system brought stability to networks. But, oh how the times have changed. By now, you know that Microsoft will not offer any additional support after today because let’s face it – Windows XP is on its way to becoming a relic at least in technological terms.
Do you remember waaaay back in 2001 when Windows XP first came onto the computer scene? Everyone thought it was fantastic. The interface was a drastic change from the previous versions, it was packed with features, and the security of the system brought stability to networks. But, oh how the times have changed. By now, you know that Microsoft will not offer any additional support after today because let’s face it – Windows XP is on its way to becoming a relic at least in technological terms.
How many of you out there just can’t stop clinging to Windows XP? There are quite a few of you that are refusing to let go, and you’re not alone. Microsoft wants you to let go, and even in some cases, is offering a $100 discount to switch to Windows 8. If that isn’t appealing enough to switch, think about the fact that you’ll no longer get security updates or have anyone at Microsoft that you can call when Windows XP just isn’t behaving right.
Still not convinced? Then, 24HourSupport at least wants to offer you help until you’re able to take the plunge. On our help pages, you’ll find Windows XP ranging from setting up a dial-up connection (remember those?) to connecting to your wireless network. You can even view information on all of the other Windows operating systems just in case you’re curious.
Need to chat about Windows XP? Don’t forget to contact us, and we’ll work to assist you with any issues that you may be experience. Long live XP!
The Heartbleed Bug: What You Need to Know
 Valentine’s Day has come and gone, but you’re probably hearing talk of something called Heartbleed, right? For those of you who aren’t sure whether to break out the chocolates or just ignore it, this is something that should definitely get your attention. Heartbleed is a vulnerability in the OpenSSL software that can create security issues for applications and content on the Internet that are using SSL and TLS encryption.
Valentine’s Day has come and gone, but you’re probably hearing talk of something called Heartbleed, right? For those of you who aren’t sure whether to break out the chocolates or just ignore it, this is something that should definitely get your attention. Heartbleed is a vulnerability in the OpenSSL software that can create security issues for applications and content on the Internet that are using SSL and TLS encryption.
Under most circumstances, SSL/TLS encryption is in place to ensure that your personal information is not compromised, but the vulnerability in the OpenSSL software can allow hackers to get around the security features of the encryption. Your credit card numbers, login names to websites, passwords, and other data becomes at risk and can be stolen through processes that can go undetected.
Because Heartbleed has become a widespread issue, a security patch was announced on Monday detailing the findings and what websites using OpenSSL should do. Server administrators using the tool should apply the patch as soon as possible as the vulnerability can create potential threats when using the Internet for tasks such as online purchases, email, and instant-messaging (IM) applications.
Most websites using OpenSSL have likely already patched their sites, but if you’re still not sure what you should do as an Internet user, here are some general guidelines you can following:
1) If a website has the potential to be affected by Heartbleed, vendors are communicating with their users, so be on the look out for any news or announcements. Social media accounts for these websites is a good place to start. You can use this list of popular websites to find those using OpenSSL that can be affected.
2) Change your passwords. Make sure that you choose secure passwords that are not easily guessed and follow any password guidelines that are provided.
3) Once your passwords are changed, continue to monitor your personal information and the accounts and websites that are used for anything unusual.
Help Downloading Apps from Google Play Store
 Have a new Android mobile device and have gotten stuck on what you need to do to download apps from the Google Play Store? We want to help! Below, you’ll find quick tips on getting started and hopefully, you’ll be downloading apps until your phone reaches capacity or you just decide to quit — whichever comes first!
Have a new Android mobile device and have gotten stuck on what you need to do to download apps from the Google Play Store? We want to help! Below, you’ll find quick tips on getting started and hopefully, you’ll be downloading apps until your phone reaches capacity or you just decide to quit — whichever comes first!
1. Make sure that you have a Google account.
If you’re using Gmail, then you’re all set since Google provides you with the capacity to access all of its services with one login. If you don’t use Gmail or any other Google services, then you can sign up for an account here.
2. Find the Google Play Store app on your Android mobile device.
Google Play only runs on Android 2.2 and up, so if you have an older device, it’s probably not available.
3. Set up your payment method.
There are several free apps in the Google Play Store, but for those that require a fee, make sure you set up your account with your preferred payment method. You can find a list of available methods here.
4. Search for the app that you want to download.
If you’re looking for Bubble Mania, simply type in the name of the app in the search feature to locate the app. If you’re not sure of the name of the app or are just looking to browse, the Google Play Store offers several categories to choose from and also offers the option to select from categories such as new releases and what’s popular.
5. Download and enjoy your app.
Now that you’ve downloaded the app that you’re looking for, it’s time to put that “hard work” to use and enjoy your app!
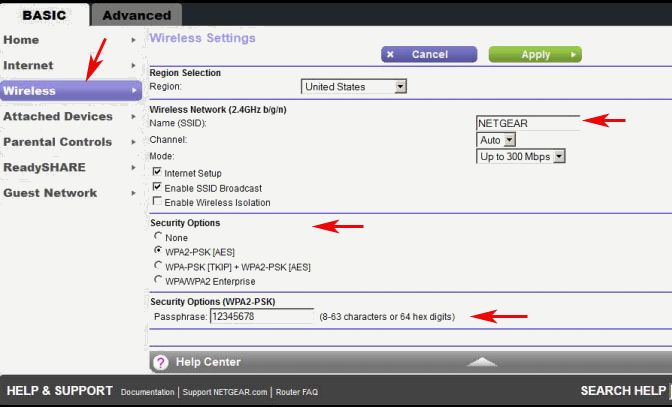
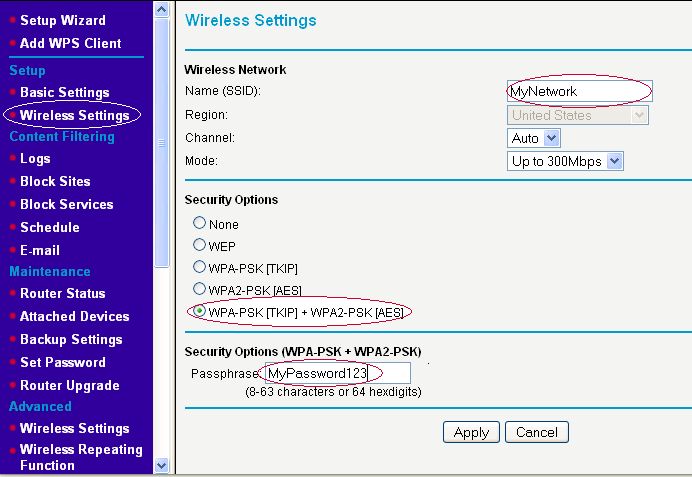
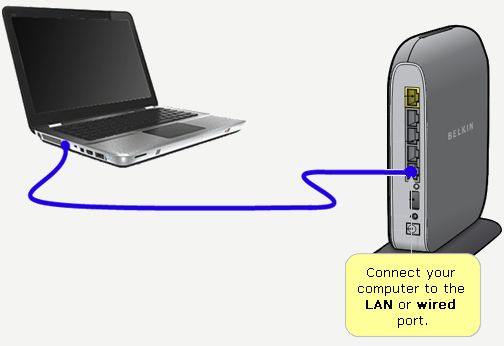
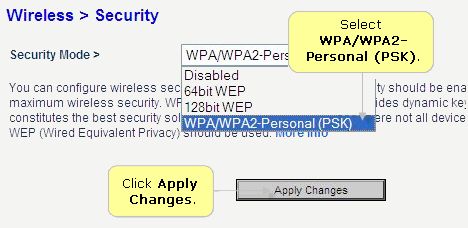
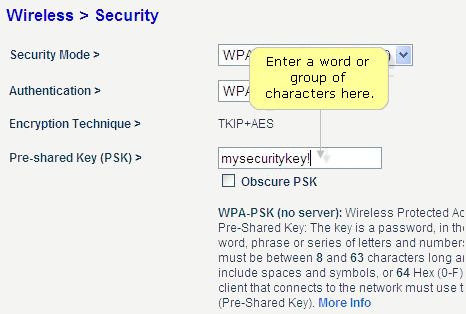
Why Should I Choose WPA or WPA2 for My Wireless Security?
 Know anyone with a wireless home network? Or, should we say do you know anyone that doesn’t have a wireless home network? Nearly everyone is connecting wirelessly at home with some gadget, computer, or device, so staying safe is a high priority. You may be confused about wireless security and trying to get it set up, so we wanted to make sure that you know where to begin.
Know anyone with a wireless home network? Or, should we say do you know anyone that doesn’t have a wireless home network? Nearly everyone is connecting wirelessly at home with some gadget, computer, or device, so staying safe is a high priority. You may be confused about wireless security and trying to get it set up, so we wanted to make sure that you know where to begin.
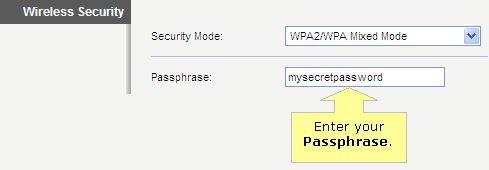
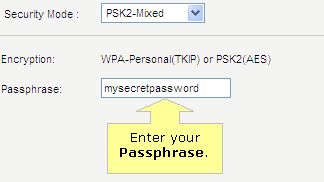
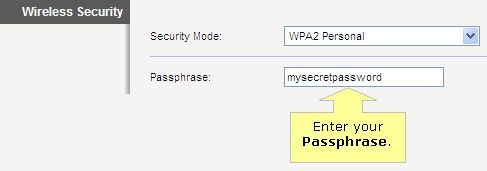
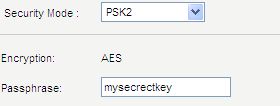
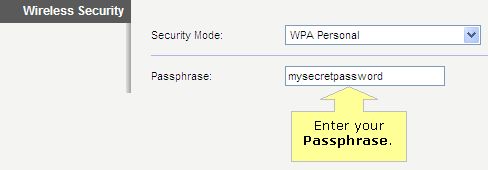
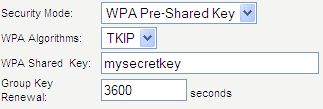
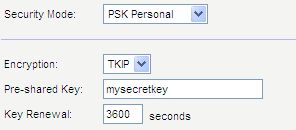
Most wireless routers that you purchase will likely have wireless security options to select when setting them up. You’ll probably start seeing acronyms like WEP and WPA and may not have a clue what they mean, and that’s okay. In previous years, WEP (Wired Equivalent Protocol) was the popular security type to choose. It was easy to set up and seemed secure, but with the changing times and security threats at an all time high, something more secure was necessary. In steps WPA (Wi-Fi Protected Access), which has proven to be a better security option.
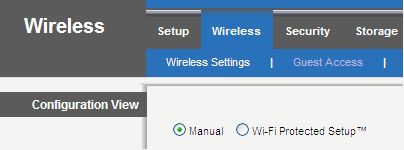
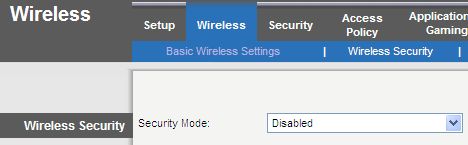
Since you already have your wireless router, we thought we’d help you out with enabling WPA or WPA2. Here is some info from popular router vendors:
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start blogging!

 .
.
 .
.
 .
.