Online Identity Theft
There are thieves on the Internet that will try to steal your sensitive information. Don’t make it easy for them. A shopping spree, a trip to an exotic island and a slew of credit cards to cover any extra expenses. This may be a dream for most, but if the person running up the charges has stolen your identity, it could be a nightmare for you. Identity theft is one of the fastest growing crimes in the U.S, and the Internet has given identity thieves a whole new way to find victims.
Every silver lining has a cloud
The Internet is a great resource, and it has changed the way we do business. More people every day are conducting business online by buying products, paying bills, taking courses, and even selling things to others through Internet auctions. Unfortunately, when a great new thing comes along, there are people out there that will look for new ways to take advantage of others. The Internet is no exception. Cyber thieves are using cleverly crafted deceptions to steal sensitive information from unsuspecting people like you.
One popular tactic is known as “phishing”, where Web-savvy crooks will send out mass emails that look as if they are from a well known company. These emails ask you to supply information like credit card numbers, account numbers, passwords, social security numbers, date of birth, and other sensitive data that you should never give out to unauthorized individuals. The identity thieves pick web sites that have large numbers of customers, since that will increase the likelihood that a recipient actually uses their service and will believe that the email is legitimate. Company names like eBay, Best Buy, and PayPal have been used as lures, and untold customers have unwittingly sent their personal information to the identity thieves.
Here is an example of just such an email sent by someone “phishing” for personal information. It was cleverly laid out to look like an official notice from eBay.
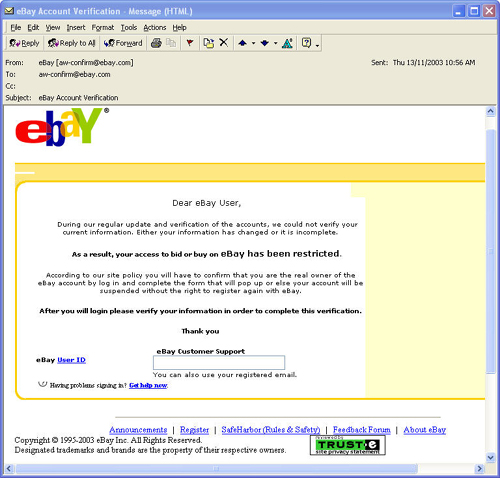
As you can see, the email looks legitimate, and would likely fool someone who uses eBay’s services.
The link in the email sent the user to the following page to collect personal information.
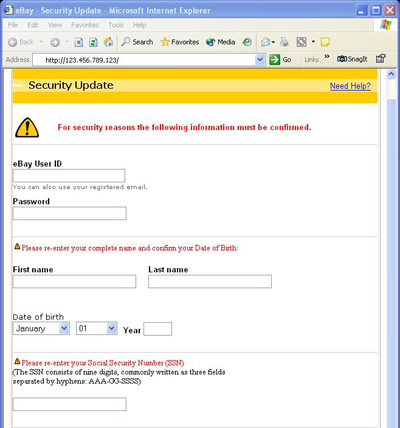
In addition to the above data, the Web site went on to ask for the user’s credit or debit card information and even their ATM PIN number. A day later the site was gone, and the thief who created it made off with the personal information of anyone who responded.
Phishing with VoIP
Another new tactic is called “Vishing”, which is the use of a Voice over IP (VoIP) account and auto dialer to make mass telephone calls. In this scheme, the victim would receive a telephone call from an automated system, supposedly from a bank, credit card company, or other service provider, asking them to confirm their account information by punching it in, or by calling another number and doing the same. The unsuspecting person dutifully follows the instructions and enters their account number or other sensitive data (such as social security number, birth date, etc.). The identity thief’s system records the numbers, which would then allow them to use that account, or use the stolen information to open other accounts in their victim’s name.
VoIP accounts cost almost nothing, and can be quickly opened by anyone with little documentation. They can be closed just as quickly, and they are easily spoofed, which makes it very hard to track down the thieves. The easiest way to protect yourself from this scheme is to never use a phone number provided in a phone message, email, or from any other unsolicited communication. If you receive a call like this and are not sure whether it is valid, you should instead call the number printed on the back of your credit card or on your monthly statement to check it out.
Tried and true methods
Of course, even in this high-tech world, the old fashioned ways of stealing your personal information are still around. Crooks still steal wallets and purses, giving them instant access to credit cards, checkbooks, and personal information. Trash is another source. If not disposed of properly, it could yield receipts or documents that may have credit card numbers, social security numbers or bank information. Others, even more daring, will steal mail out of unlocked mailboxes. In addition to finding information in your mailbox that can be used to steal your identity, mail thieves have perfected the art of “check washing”. The ink can be removed from any checks you have written using readily available household chemicals. Once the check has dried, it can be rewritten for any amount to another payee or to CASH.
More Information: Learn more about protecting yourself from identity theft
